Knowledge Byte: Security at Every Layer When Developing For the Cloud

Cloud Credential Council (CCC)

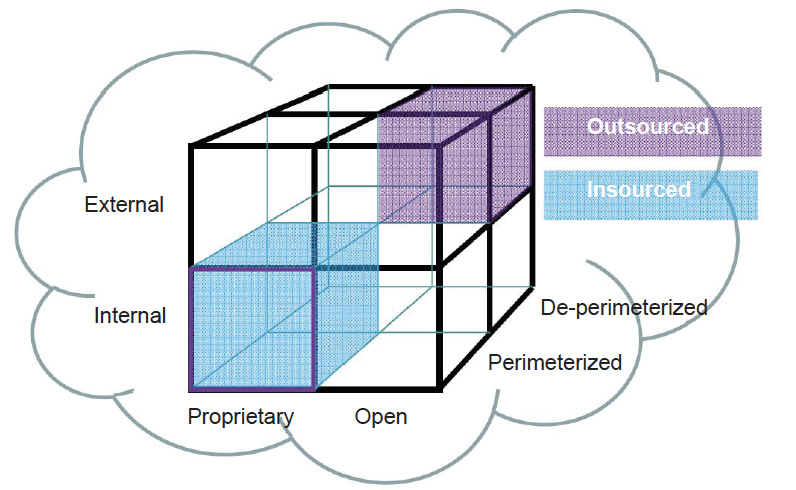
In network security, de-perimeterization is a strategy for protecting a company’s data on multiple levels by using encryption and dynamic data-level authentication. Network administrators commonly use a castle analogy to explain their security strategy. Network devices are placed behind a firewall and security efforts are focused on keeping intruders out. Thus, company data is protected on the perimeter. With the advent of web services, ubiquitous connectivity, and a mobile workforce, however, some administrators are beginning to question whether the traditional border model of IT security is practical.
The term de-perimeterization was coined by Paul Simmonds of the Jericho Forum, a non-profit group dedicated to “the development of open standards to enable secure, boundaryless information flows across organizations.” Simmonds says that a hardened perimeter security strategy is impossible to sustain and is fundamentally at odds with an agile business model.
The Jericho Forum has identified the following four dimensions to differentiate cloud formations from each other:
● Internal/External
● Proprietary/Open
● Perimeterized/De-perimeterized
● Insourced/Outsourced
The following figure depicts the security features for each layer of the enterprise perimeter:
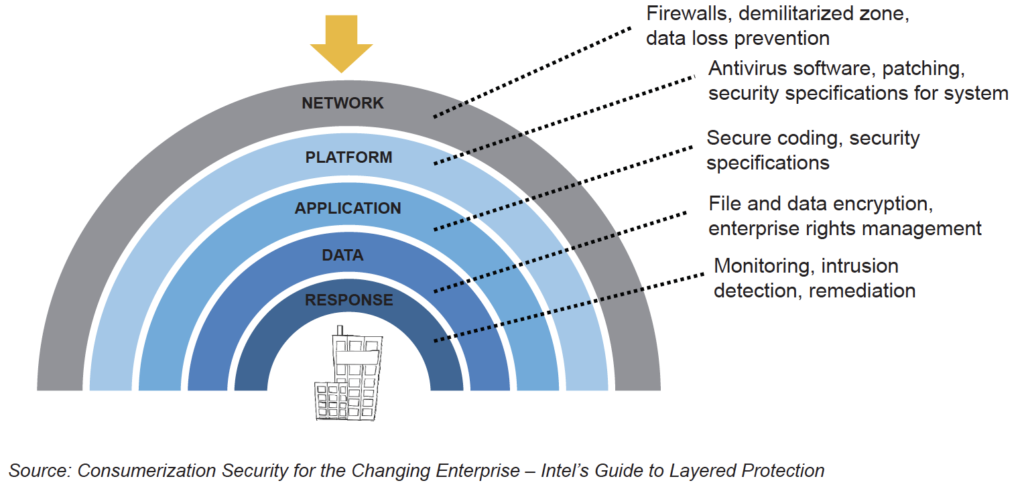
The hardware-enhanced security provides layered protection for every perimeter of a business, including:
● Network: Use authentication technologies to provide access only to known, trusted users.
● Platform: Stop attacks and protect online transactions with added protection below the operating system.
● Application: Guard against escalation-of-privilege attacks and secure virtualized models.
● Data: Protect sensitive business data with faster full-disk encryption and anti-theft capabilities.
● Response: Remotely diagnose, isolate, and repair infected clients in any operational state.
Courses to help you get
results with Cloud
Professional Cloud Developer™
The industry-recognized CCC Professional Cloud Developer certification is based on the Cloud standards developed by NIST and includes best practices on application design for Cloud environments. Importantly, it supports many vendor technology solutions, covering Open Source and major vendor standards. We made sure to include various high-quality reference materials to help you in your career…
Never miss an interesting article
Get our latest news, tutorials, guides, tips & deals delivered to your inbox.
Keep learning




