Knowledge Byte: An Introduction to Protecting Data in the Cloud

Cloud Credential Council (CCC)

Data handling is a major issue for organizations today. Most organizations do not have mature data classification processes, single source of truth for their data, and/or understand the value of their data until lost.
Organizations moving data into the cloud need to understand the importance of their data and then how can they secure their data properly both on-premise and within the cloud services.
Data can take many forms. For example, for cloud-based application development along with the development tools, it includes application programs, scripts, and configuration settings.
For deployed applications, it includes records and other content created or used by the applications, including de-allocated objects, as well as account information about the users of the applications.
Access controls and encryption are the means to keep data away from unauthorized users. As we learned, access controls are typically identity-based. This makes authentication of the user’s identity a very important issue in cloud computing. Due to a lack of physical control over the storage of information, encryption may be the only way to ensure that data is protected.
Data Protection: Primer
Organizations need to understand their data protection requirements, policies, and security responses/ capabilities. The major elements, which need to be understood prior to moving workloads to cloud, are as given:
● Data protection requirements
● International data protection elements
● Data governance
● Data protection/security policy
● Data classification
● Data discovery
● Data classification enablement
● Understanding data relationships
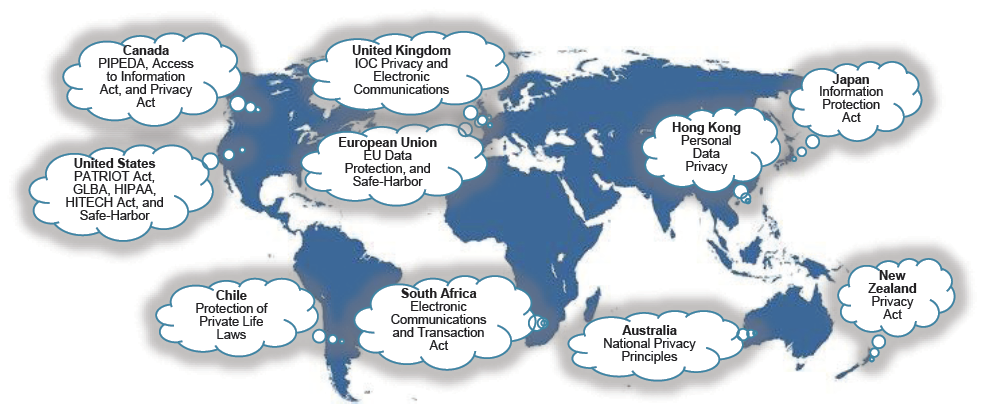
Data Protection Requirements
There are a number of regulations, standards, and frameworks, which can impact data on cloud computing. Security personnel needs to understand these laws and protection requirements as they are related to geography, access, and protections: at rest, in use, and in transit.
Courses to help you get
results with Cloud
Sorry, we couldn't find any posts. Please try a different search.
Never miss an interesting article
Get our latest news, tutorials, guides, tips & deals delivered to your inbox.
Keep learning



